By default, Linux systems allow both password-based and key-based authentication over SSH. If you have a server with SSH open to the world, password-based authentication shouldn’t be allowed at all.
To disable password-based authentication, edit the SSH config file:
nano /etc/ssh/sshd_config
Add the following lines:
PasswordAuthentication no
PubkeyAuthentication yes
Now generate a new private/public key pair:
ssh-keygen
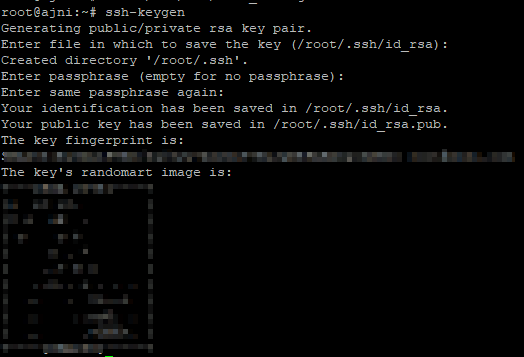
id_rsa is your private key
id_rsa.pub is the public certificate thumbprint that must be added to ~/.ssh/authorized_keys
nano ~/.ssh/authorized_keys

The SSH service must be restarted.
service ssh restart
Now you can connect to your server with key-based authentication only. If connecting from a Linux system the file’s permissions must be set to 600.
chmod 600 id_rsa
ssh -i id_rsa ip@username
If you like using Putty, you’ll have to load the file with PuttyGen and save the private key as .ppk.
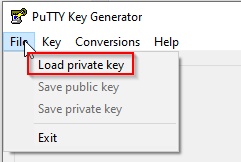
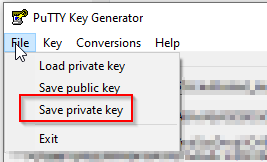
PuttyGen can be downloaded here: https://www.chiark.greenend.org.uk/~sgtatham/putty/latest.html
Links:
https://askubuntu.com/questions/346857/how-do-i-force-ssh-to-only-allow-users-with-a-key-to-log-in
