Apache Virtual Hosts are great because they let you host multiple websites on the same server. The public IP address can also be re-used – Apache knows, based on the HTTP host header, which website to show.
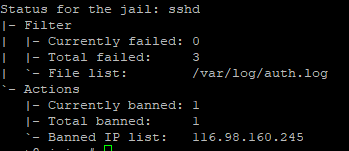
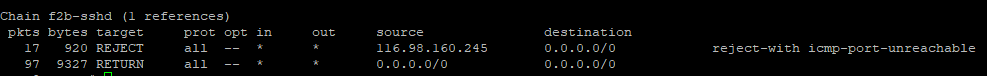
But have you considered this scenario? website1.com gets compromised and some malicious person has access to the server. What can they do? Most certainly they have access to every other website on the server because, by default, every Virtual Host runs under the same user www-data. Fortunately, there is a module that allows us to use different users for every Apache2 Virtual Host called apache2-mpm-itk.
It is very easy to install:
apt-get install libapache2-mpm-itk
a2enmod mpm_itk
If you face any issues, disable mpm-prefork and try enabling mpm_itk again.
a2dismod mpm_prefork
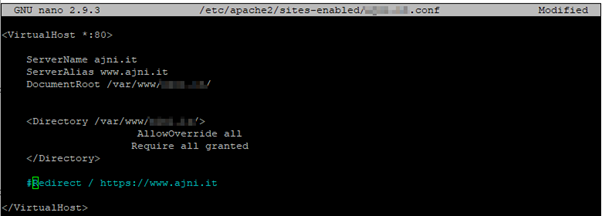
Now, in the Virtual Host config file, insert these lines (user www-site1 and group www-site1):
<IfModule mpm_itk_module>
AssignUserId www-site1 www-site1
</IfModule>
The user could be added with useradd:
useradd www-site1
Lastly, give owner rights to the new user and no one else.
chown www-site1:www-site1 -R /var/www/site1
Or even better, give the www-site user write rights on the upload folder. Everything else is readable only.
find /var/www/site1/ -type d -exec chmod 0755 {} \; #Change directory permissions rwxr-xr-x
find /var/www/site1/ -type f -exec chmod 0644 {} \; #Change file permissions rwxr-xr-x
chown ajni:ajni -R /var/www/site1/ # Let your useraccount be owner
chown www-site1:www-site1 -R /var/www/site1/uploads/ #Let apache be owner of upload folder
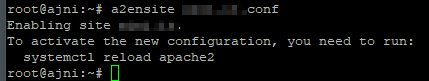
Oh yeah. Don’t forget to restart apache:
service apache2 restart
References:
https://cloudkul.com/blog/apache-virtual-hosting-with-different-users/